SSH is by itself a secure way to connect to a remote device. However, if you're still keen to add additional security to your SSH connection, you can add two-factor authentication to prompt you for a random verification code when connecting via SSH. We've previously explained this. How to do this on different social networks Here we show you how to add two-factor authentication to your SSH connection.

Note: These instructions are based on Ubuntu Server. If you're using another distribution, some commands may differ.
Install two-factor authentication for SSH
Open a terminal session on the device where you will install two-factor authentication, type the following:
sudo apt install ssh libpam-google-authenticator
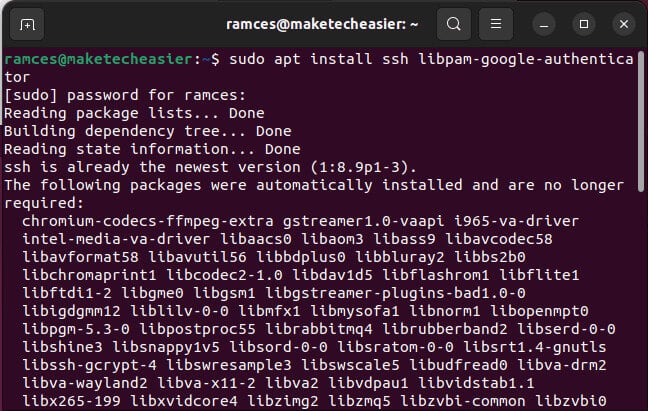
To complete the installation, run:
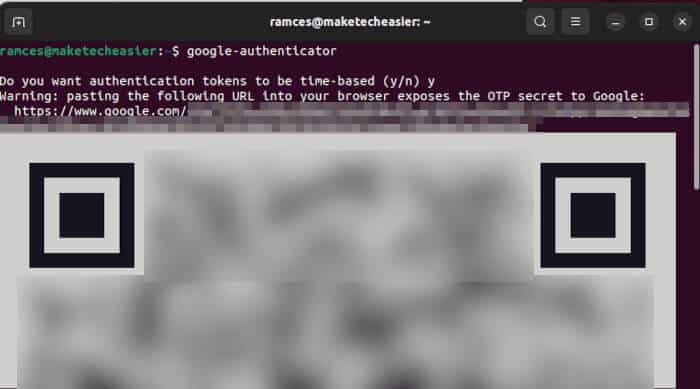
google authenticator
Tip: Learn how to use SSH X redirection to run remote applications.
Configure two-factor SSH authentication
You'll be asked a series of questions. In most cases, you can type "y" (yes) as the answer. Any time the settings are incorrect, press Ctrl+C, then type Google-Authenticator again to reset the settings.
- The program will ask you if you want the authentication codes to be time-based. To do this, click Y ثم Enter.
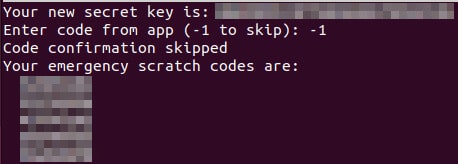
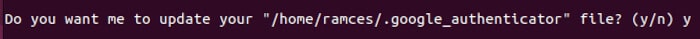
After this question, you should see your secret key and emergency code. Record and save the details. You'll need the secret key to set up the Google Authenticator app later. - The program will ask you if you want to Update the file “/home/username/.google_authenticator”. Click on Y ثم Enter.
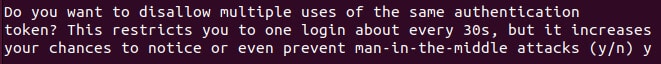
- When asked if you want to disallow multiple uses of the same authentication token, this will restrict you to only one login each. 30 secondsThis can be useful if you want to ensure that only one active connection can use the authentication token at any time.
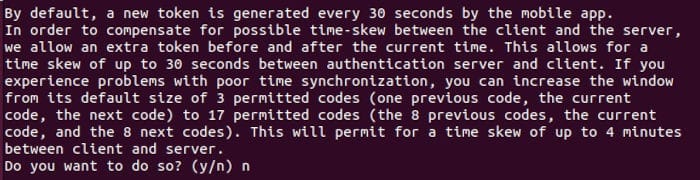
- By default, authentication tokens are only valid for 30 seconds. To compensate for a possible time lag between the client and the server, we increased the window from its default size of 1-1/2 minutes to about 4 seconds. This can be useful in cases where the clock on your local machine or the remote server is out of sync.
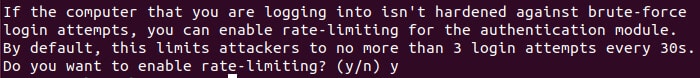
- Enable rate limiting for the authentication module. This option limits attackers to no more than 3 login attempts every 30 seconds.
Configure SSH to use Google Authenticator
- open file “/etc/pam.d/sshd”:
sudo nano /etc/pam. d/sshd
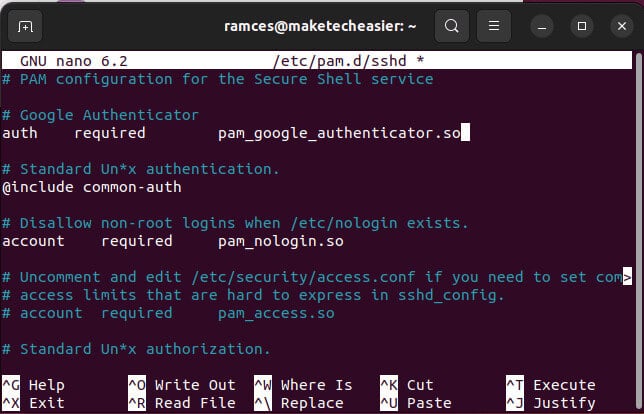
- Add this line to the top of the file:
auth required pam_google_authenticator.so
- Click on Ctrl + O and Ctrl + X To save the file and exit.
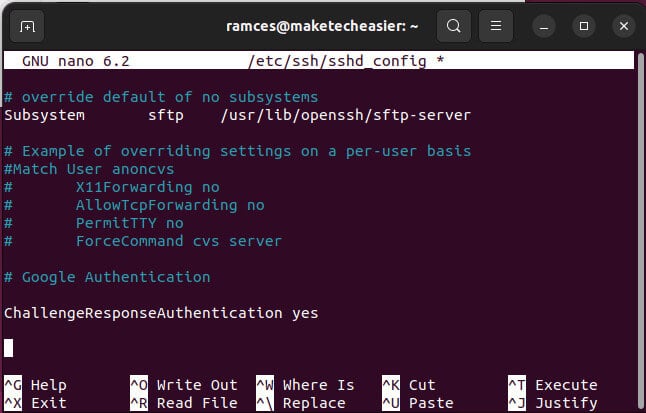
- Open The file “/etc/ssh/sshd_config”:
sudo nano / etc / ssh / sshd_config
- Scroll down to the bottom of the file and type the following line:
Eat ChallengeResponseAuthentication
- Save and exit the file.
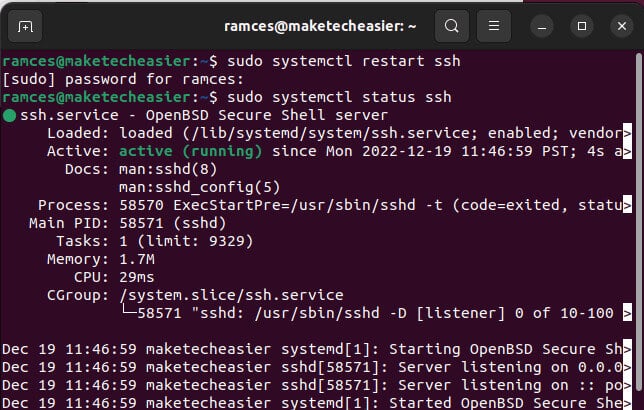
- Restart ssh server:
sudo systemctl restart ssh
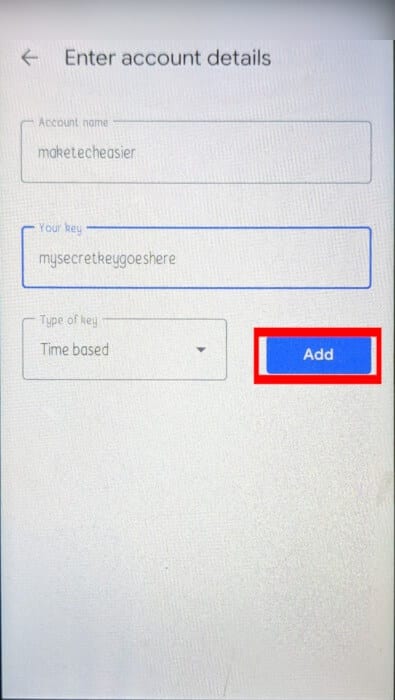
Set up a key in Google Authenticator
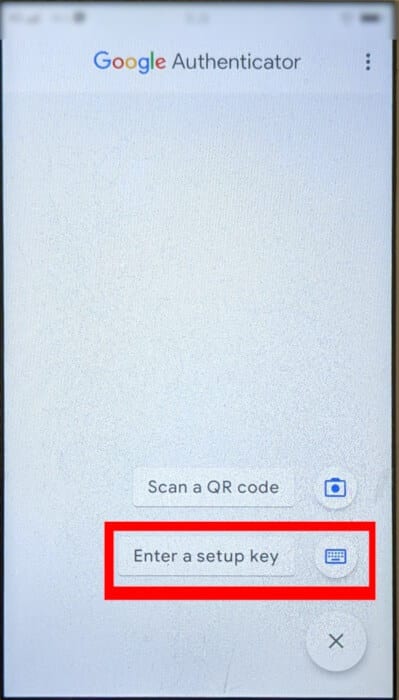
- Open Google Authenticator app (or one of its alternatives) on your smartphone (or desktop). Tap the Plus icon in the lower left corner of the app and select “Enter setup key.”
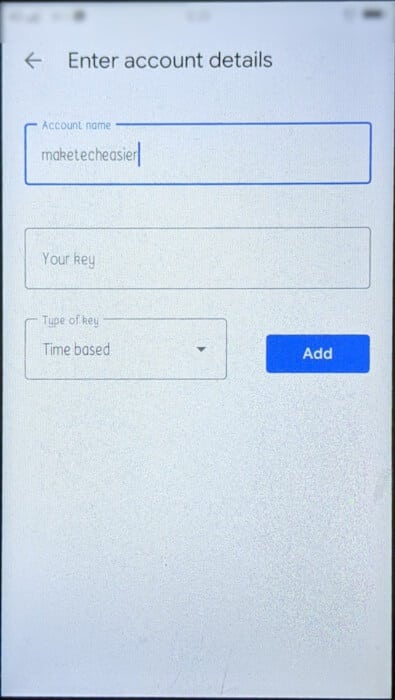
- Enter a name for your authenticator app.
- Type the secret key you created earlier and press "addition".
When you connect via SSH to the remote computer, you will see a request for a verification key.
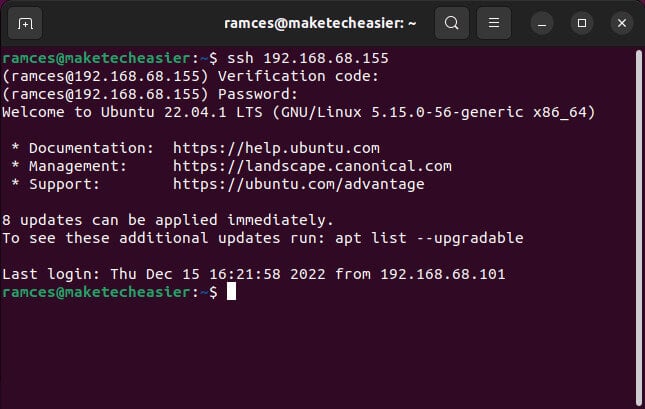
Note: Two-factor authentication only works with password-based logins. If you already use Public/private key for your SSH session This will bypass two-factor authentication and log you in directly. Also, check out more ways to secure your SSH server.
Frequently Asked Questions
Q1. I'm using Yubikey. Can I still use two-factor authentication with SSH?
answer. No. The Google Authentication module only works with standard SSH password logins. Similar to setting up a public SSH key, this specific module cannot be used with other third-party two-factor solutions, such as Yubikey.
Q2. Is it possible to use the same authentication key on a different phone?
answer. Yes. You can easily use a different phone with Google Authenticator as long as you have either your secret key or its QR code. However, you need to ensure that you have completely removed your authentication key from the previous device before importing it to a new one, as any bad actor with access to the previous device would be able to bypass your two-factor authentication.
Q3. Can you use a different two-factor authentication app with SSH?
answer. Yes. While the developers of the libpam module designed it specifically to work with Google Authenticator, you can still use it with other authentication apps, since the two-factor secret key format is often the same across different apps.