Windows processes play a crucial role in the proper functioning of your computer or laptop. Some of them, such as csrss.exe and winlogon.exe, are so critical that if you decide to end them by mistake, you could end up crashing your machine. Malware authors take advantage of this vital importance to infect healthy Windows systems. The premise is that viruses, adware, spyware, and Trojans can be called anything—even standard Windows system processes.

How to tell if Windows processes are legitimate
There are two ways to check whether Windows processes are legitimate or a source of malware: through their application properties and using third-party tools like CrowdInspect by CrowdStrike.
1. Verify the legitimacy of Windows processes through their properties
All authorized Windows process files are connected to Microsoft, the official software/app developer or a built-in Microsoft account like TrustedInstaller.exe, which controls folders like WindowsApps.
To determine if a Windows 11 or 10 process is legitimate and not a source of malware, you need to look under the hood at its application properties. Go to the tab "the details" Look for the official copyright holder for the process. If it's Microsoft, an app developer, or TrustedInstaller, you're good to go.
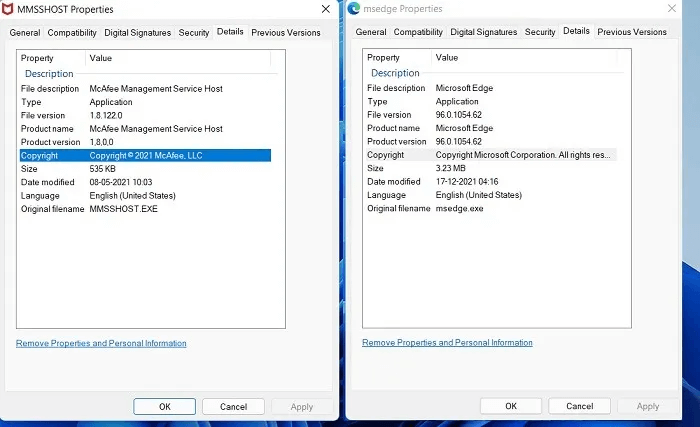
Also in Windows 11/10, you can check the tab Digital signatures For transaction specifications, you'll find official digital signatures with the latest timestamps here, giving you an extra layer of assurance.
Because the driver signature for these processes Requires standard Microsoft permissions (Moreover, any unauthorized access to the root of the device is prevented by UEFI Secure Boot), it is now impossible for malware authors to forge digital signatures in Windows 11.
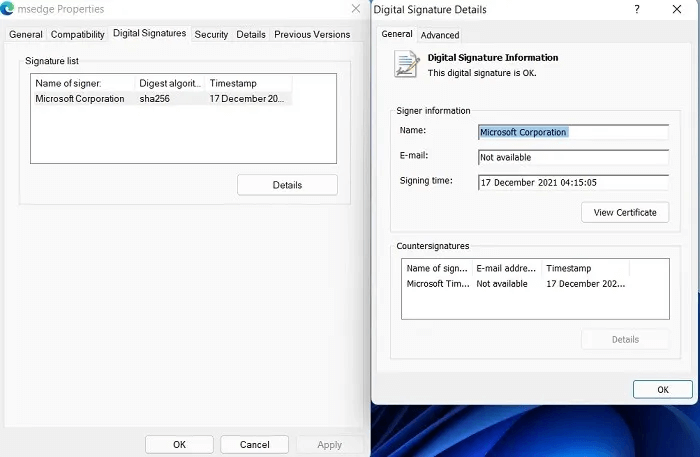
From ordinary to extremely important, such as: services.exe Or “svchost.exe” All Windows 11 operations are digitally signed using timestamps. This authentication is verified with each successful Windows update.
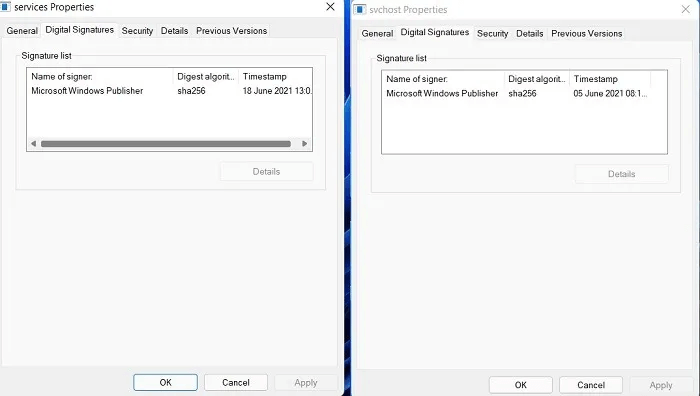
On the other hand, Windows 10 process properties may have a missing Digital Signatures tab altogether. Also, some processes may not display copyright information correctly.
However, even in Windows 10, task-critical internal system processes such as Winlogon.exe always display this information. You can verify the authenticity of the software through other means. Additionally, if you install unsigned drivers in Windows 10 or 11, no digital signatures will appear upon subsequent reboots.
2. Verify the legitimacy of Windows processes using CrowdInspect
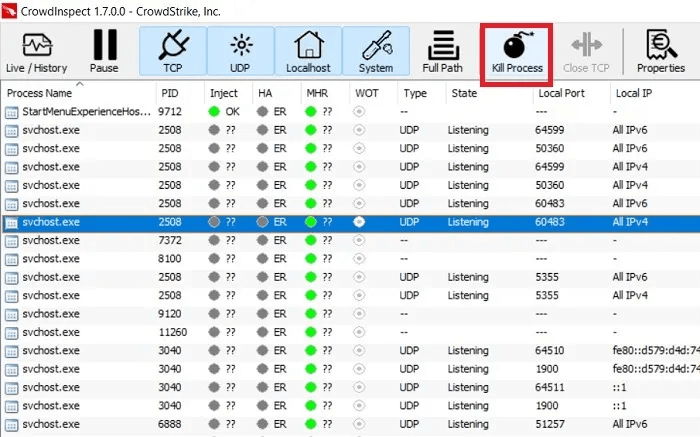
In both Windows 10 and Windows 11, you can check the health of a process file using a third-party software application: CrowdInspect by CrowdStrike. CrowdInspect is a free, host-based, real-time process inspection tool that scans for malware in the background using detection engines like VirusTotal.
- Download the CrowdInspect ZIP file from the official link Click on the extracted program to run it. You don't need to install anything.
- Accept the license agreement and proceed to the screen where you can perform a hybrid analysis of all background processes on your Windows machine. Use the built-in API key and click "OK".
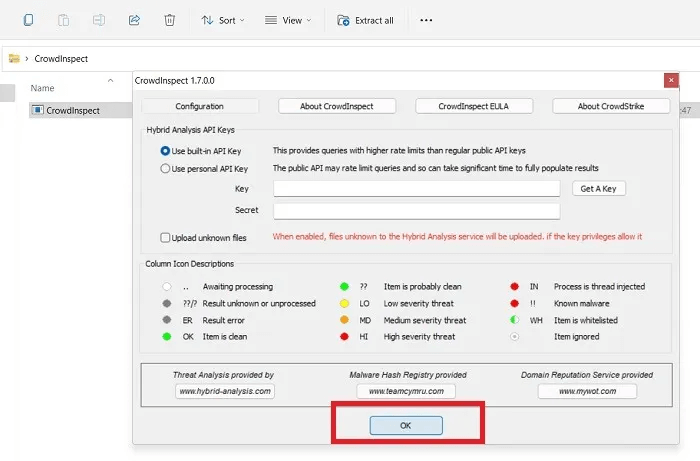
3. Wait while CrowdInspect fills your screen with a full list of background programs and processes on your Windows machine.
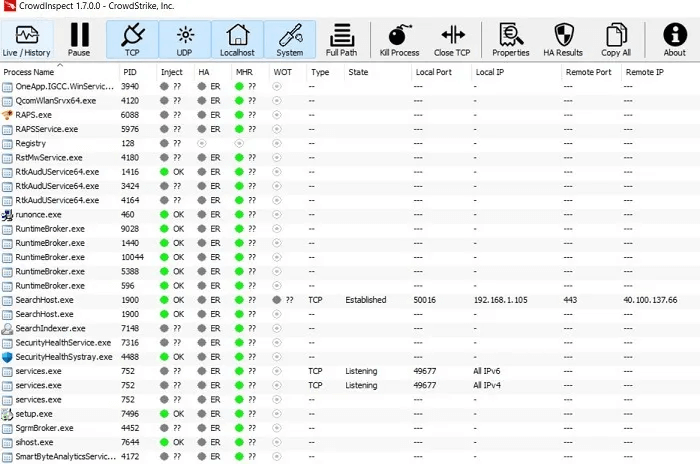
You can check the status of your programs by color codes. Any clean item is indicated by a green icon. If there are any doubts, you'll see question marks next to the icon. For low-risk items, there's a yellow icon. High-risk items are indicated by a red icon. You won't see any yellow or red icons if your device is healthy.
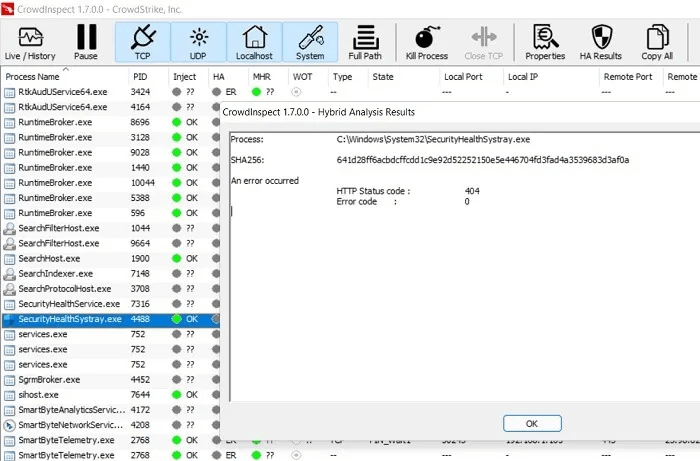
4. To further verify that there are no malware concerns, right-click on the process and click “View HA test results”You shouldn't notice any errors, which is a safe indication that you're not dealing with any malware.
List of common Windows 11/10 processes that resemble malware
1. Explorer.exe
The universal Windows File Explorer program, explorer.exe, is easily accessible from the taskbar and desktop. Its primary purpose is to act as a file manager for all files and folders on a Windows 11/10 device. Due to its vital importance, explorer.exe is a favorite target for attackers.
Virus detection: Malware typically appears as explorer.exe files, Trojans, ransomware (especially email), and Adobe Flash files. The legitimate program is almost always found in “C:\Windows”, Duplicates may appear in your D drive, program files, hidden folders, or any other computer location.
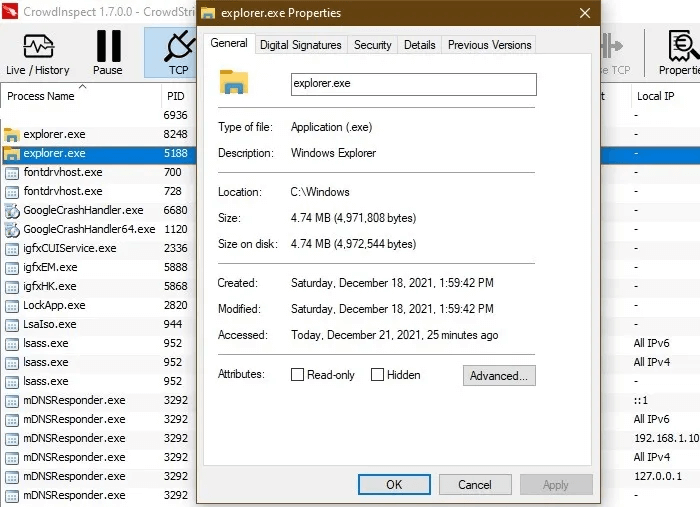
Procedure: If there are two to three instances of explorer.exe on your machine, there's no need to worry as long as they all have valid digital signatures and locations. When there are multiple processes consuming CPU, select the fake processes in CrowdInspect and right-click. "To stop the process."
2. lsass.exe
lsass.exe stands for the Local Security Authority Subsystem service, which runs behind Windows user authentication. Aside from malware, you should not terminate the original processes, as this will cause your system to lose access to Administrator accounts and local accounts , causing the device to restart.
Virus detection: A common method used by malware authors to disguise lsass is by replacing the lowercase letter "L" with the letter "I" in capital letters or uppercase letters “L.” Watch out for any deliberate spelling errors. Also, any digital signatures and invalid files located outside the folder. “C:\Windows\System32” It is a clear gift.
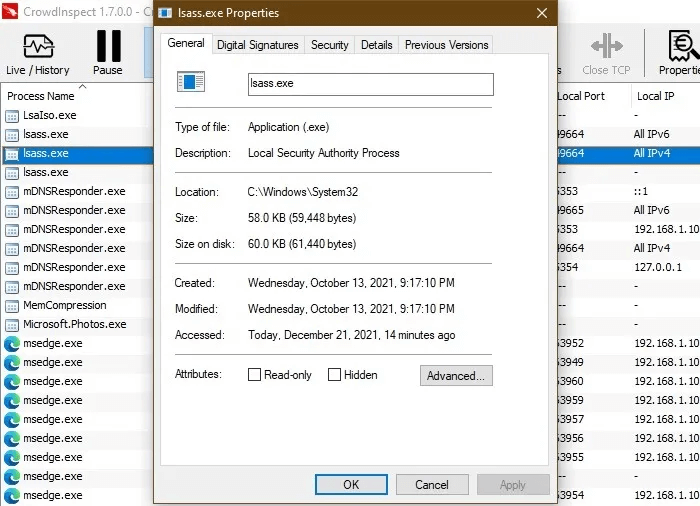
Procedure: End the pseudo-lsass processes from Task Manager. If you are not sure whether the character "L" Mother "I" Do the same from CrowdInspect. Multiple valid lsass instances are fine and shouldn't be messed with.
3. RuntimeBroker.exe
RuntimeBroker.exe is a secure Microsoft process whose job is to manage the permissions of any apps downloaded from the Microsoft Store. It verifies the authenticity of programs such as the Photos app. If an app doesn't belong on your Windows device, Runtime Broker alerts you by consuming a large amount of extra memory.
Virus detection: If your Windows machine is infected with RuntimeBroker.exe virus, you will see its presence in other computer locations other than “C:\Windows\System32.” Since the software is illegal, memory leaks will increase dramatically, putting a strain on your CPU. You'll also notice an invalid digital signature for spoofed instances.
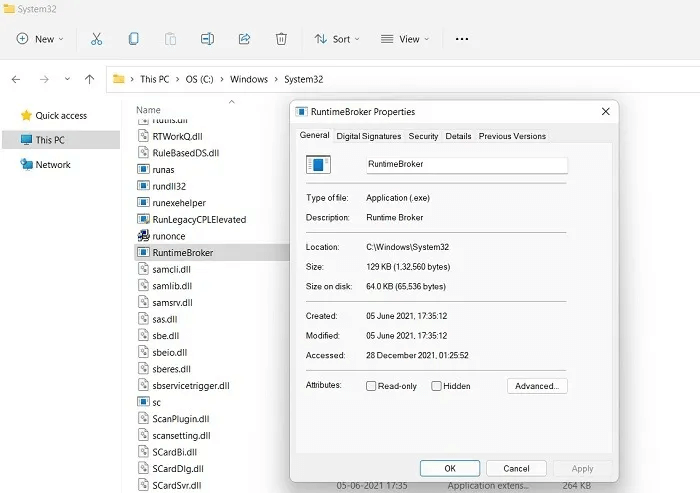
Procedure: Open Task Manager. Click Multiple instances Valid for Runtime Broker and click "Finish the job"This will eliminate any problems with a particular application. For fake RuntimeBroker.exe entries, terminate them from CrowdInspect.
4. Winlogon.exe
When it comes to Windows background processes, there's nothing more important in the scheme of things than winlogon.exe. Not only does it manage the logon process, but it also loads user profiles, controls the screensaver, and connects to multiple networks. It's located in “C:\Windows\System32.”
Virus detection: Typically a spyware or keylogger, winlogon.exe is a highly dangerous piece of malware that can cause system crashes and is easy to identify. If you have Windows Defender running, it will warn you to delete the file immediately and terminate any other vectors it uses (email, web browser).
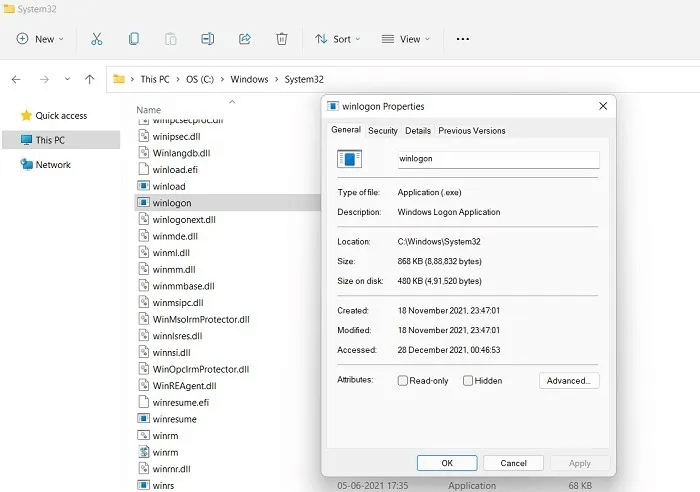
Procedure: The safe winlogon.exe executable will not have more than one instance in CrowdInspect. Other fake instances should be removed upon arrival using Windows Defender suggestions.
5. Svchost.exe file
The svchost.exe file refers to Windows Service Host , a shared service process that acts as a shell for loading various Windows services. Depending on the number of open applications, there are usually multiple instances of the svchost.exe file running as individual processes.
Virus detection: You will encounter a svchost.exe malware loop when you find a protected folder or program that is blocked by a duplicate process or spelling variants like “svhosts.exe”They are mostly ransomware or banking fraud tools. Their source vectors include PDF files, ZIP files, and JavaScript.
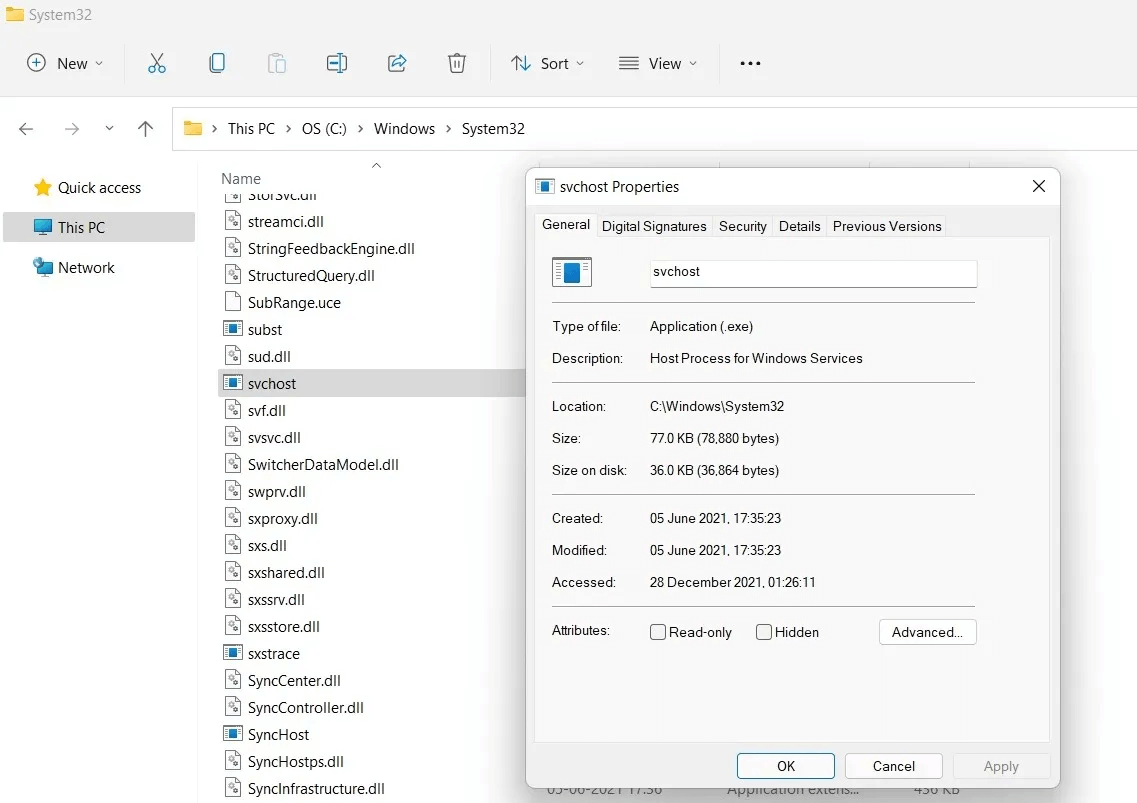
Procedure: These Trojans typically represent a low-level threat but should be removed as soon as possible. Standard antivirus tools and Windows Defender are equipped to delete any service host instances that are not present in the “C:\Windows\System32”.
6. OfficeClickToRun.exe
If you use Office tools—such as Word, Excel, or PowerPoint—you may have encountered an executable file called OfficeClickToRun.exe. Its job is to run the latest versions of Microsoft Office on your computer and handle updates. Even when it's not malware, OfficeClickToRun.exe can be a memory hog on your CPU. However, if you delete temporary files periodically, this burden will be much less.
Virus detection: Is the executable file located anywhere other than the Program Files folder in the Microsoft shared folder? The additional file is unhealthy for your system. Also, your Windows machine should only have one instance of OfficeClickToRun.exe running. Check the digital signatures of everyone else.
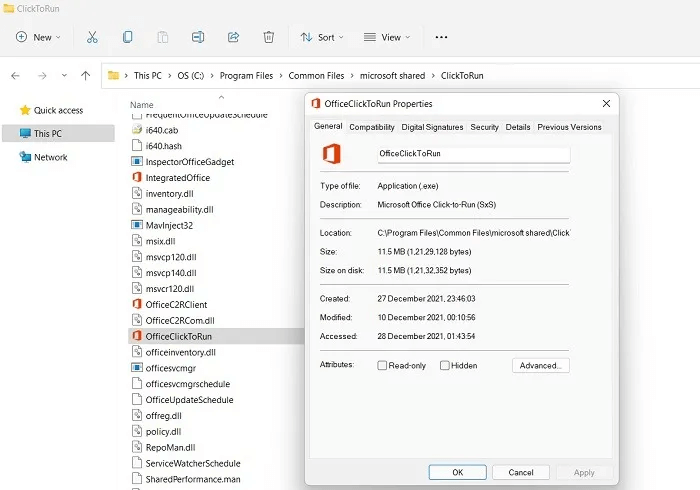
Procedure: Although not harmful in and of itself, fake OfficeClickToRun.exe instances can clog your system memory. They usually come via infected files and documents, which should be deleted immediately.
7. igfxem.exe
igfxEM.exe is an unknown background process that is essential for managing the Intel graphics card and is therefore very important for the video card's display. It comes preinstalled on your device and should be left alone, as it does not pose a burden on the system at all.
Virus detection: If you have more than one instance of igfxEM (and the spelling errors are as described), check the digital signatures. If they show Intel and Microsoft, you are not infected with malware. Otherwise, you do not have a genuine igfxEM file, and this process should be removed.
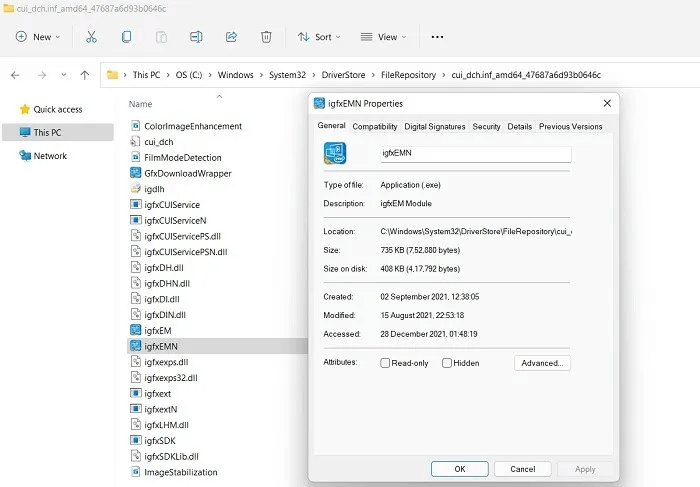
Procedure: You should not take any action if you have valid digital signatures—even with multiple Intel instances. If your original Intel graphics card appears to be corrupted, try reinstalling the driver from “devmgmt.msc”, Device Manager, in the Start menu.
8. Csrss.exe
Csrss.exe stands for Client Server Runtime Subsystem, a legitimate user process intended to manage Windows graphics activities, such as shutting down the graphical user interface and system console services. It is often mistaken for malware. Terminating it can be fatal to your system, resulting in a guaranteed crash.
Virus detection: Like other programs out there, “C:\Windows\System32” csrss.exe quietly remains in the background, and you'll only find one or two instances in CrowdInspect. Any suspicious files will have invalid digital signatures and lose copyright details.
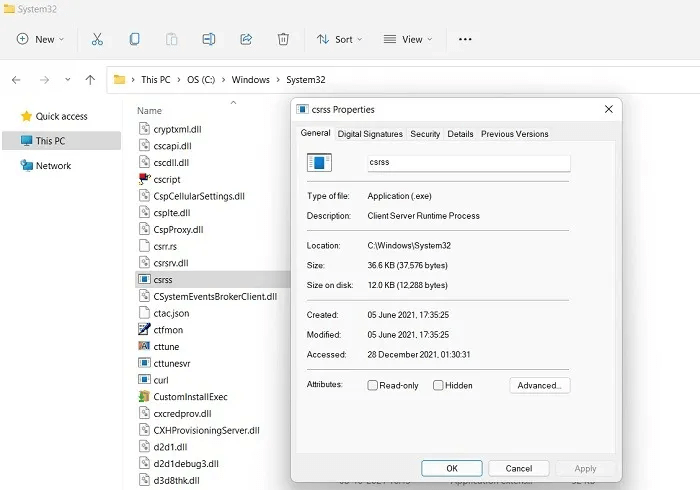
Procedure: csrss.exe is often used by rogue security software companies and tech scammers as "proof" of a machine infection. This is not real malware, so you should never terminate the current process due to bad tech advice.
9. GoogleCrashHandler.exe file
If you have any Google software on your Windows device, including Google Chrome, you'll find an executable file called GoogleCrashHandler.exe, which is part of the Google Updater package. This isn't a critical Windows component and can be safely and easily removed, but it's not always malicious either.
Virus detection: If the digital signature of Google CrashHandler.exe is invalid, i.e. it is not signed by Google, we are looking at a possible sign of spyware or rootkit infection, because the normal process is safe.
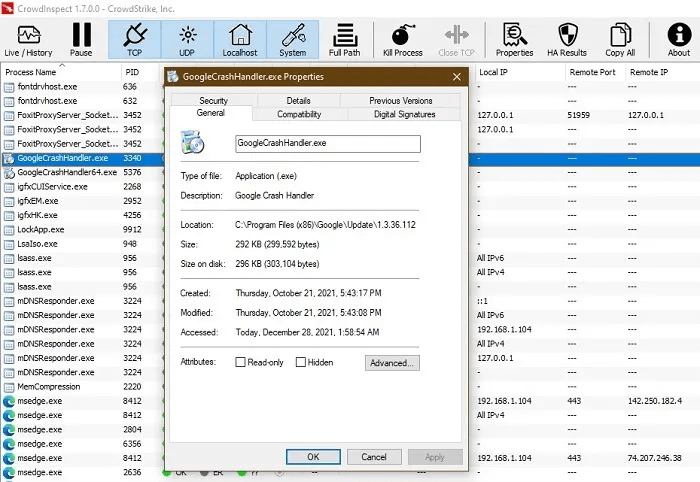
Procedure: Remove any or all instances of GoogleCrashHandler.exe from your system's task manager, even though it's not always malware. You don't want it to unnecessarily burden your CPU unless you want to send crash reports to Google.
10. Spoolsv.exe
Spoolsv.exe is a native Windows process, integrated with the Printing Spooler service, that translates fonts and graphics to printer hardware and any virtual printers. This is a core Windows process that has existed since the beginning of MS-DOS. Terminating any valid entries of the spoolsv.exe process will cause the device to fail and the system to reboot.
Virus detection: Although it resembles some malware, spoolsv.exe is a legitimate, safe Windows process. Any additional processes will lack digital signatures from Microsoft. If malware authors use a similar name to target your system, Windows Defender should alert you.
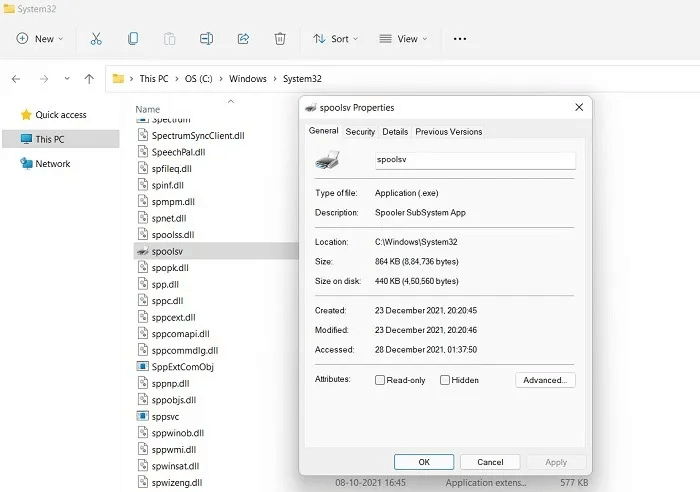
Procedure: No action should be taken if the spoolsv.exe process has been verified by a Microsoft digital signature. Otherwise, go to Task Manager to terminate the process.
11. Task Manager
The Windows Task Manager (taskmgr.exe) is a very important program that controls all core Windows processes as well as applications. Disabling this essential program and its derivatives, such as taskhostw.exe, can be fatal to your system, and malware authors are well aware of this.
Virus detection: If you feel that a program associated with Task Manager is not working properly, check its file location, which should be in “C:\Windows\System32”. Restart your device to see if the problem has resolved. If the suspicious Task Manager instance persists, we're investigating potential malware. Another sign is that its digital signature may be invalid.
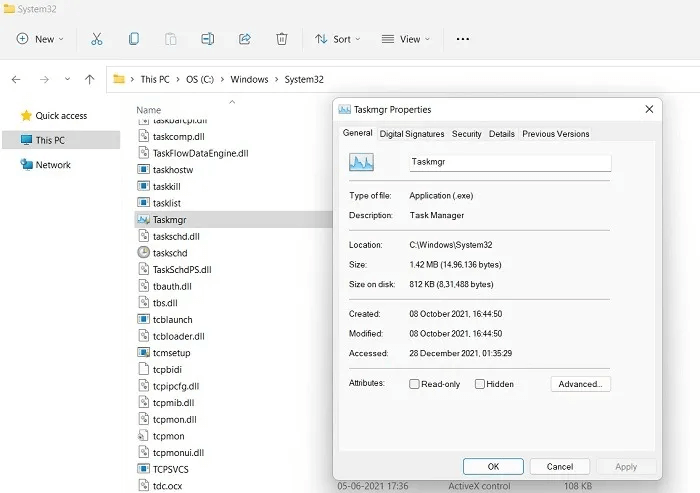
Procedure: Any can be specified. Task manager - Like the executable file - infected with malware and terminated from the Task Manager itself. However, if you are experiencing the TaskSchedulerHelper.dll error in Windows 10, take the corrective steps as described.
Summary: Warning signs of malware that resemble Windows processes
Here's a quick summary of how to handle any suspicious processes that resemble standard Windows system processes. You may or may not be dealing with malware, but it's important to keep an eye out for these warning signs.
- Check the app property details for correct copyrights: Each program in Windows 11 and Windows 10 has a file location. From there, you can access "the details" in the tab "Characteristics". Make sure the copyright belongs to Windows, TrustedInstaller, or legitimate process owners, such as Google, Intel, NVIDIA, etc. If not, we're looking for a potential source of malware that needs to be removed from your system.
- Check CPU usage for Windows Process programs: It's normal for CPU usage to increase in Windows when multiple systems are running simultaneously. However, multiple instances of the same program slowing down the system is cause for concern. Unnecessary programs should be identified and closed immediately.
- Check suspicious Windows processes for digital signatures: This is the most important and easiest way to verify the authenticity of a process. If the digital signature for a process is invalid and does not come from a trusted source, there is a high probability that it is malware.
- Check the location of the suspicious process file: Most Windows file processes have a well-defined location on your computer. It can be either “C:\Windows\System32” , program files, or some other well-defined location. You should not find instances of this process in other areas, such as drive D, as this indicates the possibility of malware.
Frequently Asked Questions
Q1. What should I do if a particular Windows process is actually malicious?
answer. No legitimate Windows process can harm your system. However, if there are repeated instances of such processes containing malware, go to CrowdInspect, right-click on the process, and then click "End the process"If Windows Defender is running, it will handle these malware cases. Read on to find out why. Windows Defender is the only antivirus you need..
Q2. What happens when a valid Windows process terminates and how do you recover from there?
answer. If you accidentally terminate a legitimate Windows process, the consequences depend on how critical the process is to your system. If it's an unnecessary software process, there will be no impact on your Windows device.
For high-impact processes like winlogon.exe and csrss.exe, Windows has a built-in mechanism to prevent accidental termination. However, if they persist and you attempt to terminate the system from the Task Manager, your computer will automatically shut down, requiring a reboot. In the worst case, this can lead to a complete power outage and permanent damage due to a crash.
If a low-impact process is an integral part of the scheduled operation and maintenance of Windows, the system will report a critical failure and Turn it off automatically. After starting The problem will go away.









